Cisco Meraki Client VPN incorporates several methods for authenticating users before they are allowed onto the network. For admins who want to incorporate an additional level of security, client VPN also allows for the use of third-party two-factor auth solutions, requiring users to go through a second authorization step. Learn best practices for setting up Cisco Meraki Client VPN, both local authentication and active directory authentication. By using the built-in Meraki dyna. This is the line that I use for my Meraki Client VPN. It does have to be run with admin credentials for -AllUserConnection to work. Your add-vpnconnectionroute lines should have an -AllUserconnection argument as well. This can be accomplished by going to Security & SD-WAN Configure Addressing & VLANs on the Cisco Meraki Dashboard and selecting the option for Passthrough or VPN Concentrator. In this mode, the MX Security Appliance acts as a layer 2 bridge and does not modify the source address of traffic that traverses the WAN uplink. You can create Site-to-site VPN tunnels between a Security Appliance or a Teleworker Gateway and a Non-Meraki VPN endpoint device under the Non-Meraki VPN peers section on the Security & SD-WAN Configure Site-to-site VPN page. Simply click 'Add a peer' and enter the following information: A name for the remote device or VPN tunnel.
1. Open Start Menu -> Search “VPN” -> Click Change virtual private networks (VPN).
2. From the VPN settings page, click Add a VPNconnection.3
3. In the Add a VPN connection dialog:
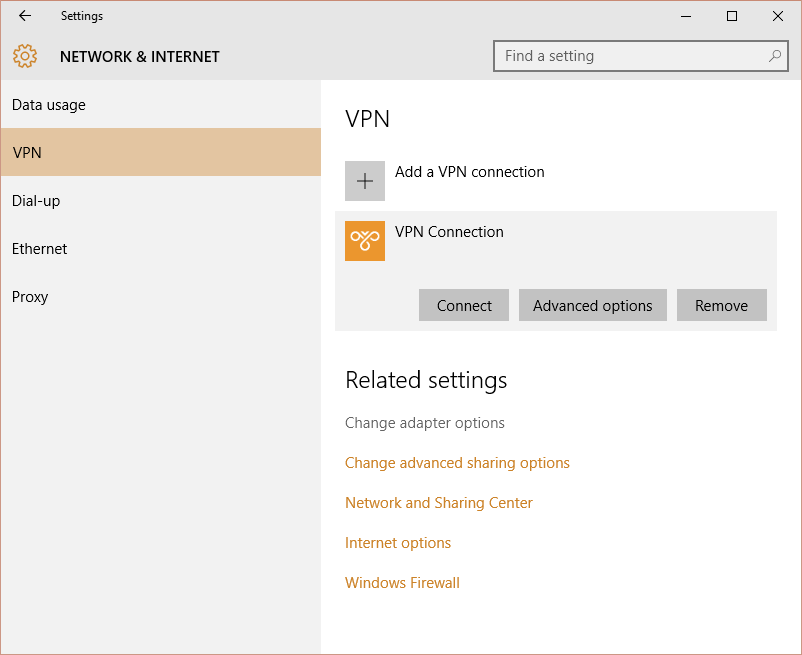
- Set the VPN provider to Windows (built-in)
- Provide a Connection name for the VPN connection.
- Specify a public IP address (found in Dashboard, under Security appliance -> Monitor -> Appliance status -> Uplink) or hostname for the Server name or address.
- Select L2TP/IPsec with pre-shared key for the VPNtype.
- Provide a User name and Password (optional).

4. After the VPN connection has been created, click Change adapter options under Related settings.
5. Right-click on the VPN Connection from the list of adapters and click Properties.
6. In the Security tab, select “Require encryption (disconnect if server declines)” under Data encryption.
Then, select Allow these protocols under Authentication. From the list of protocols, check “Unencrypted password (PAP)“, and uncheck all other options.
Despite the name “Unencrypted PAP”, the client’s password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or LAN.
7. Click on “Advances settings“
In Advanced Properties dialog box, choose “Use preshared key for authentication” and enter the same key you used for the client VPN settings in the Dashboard. Note: if you are enabling client VPN for your employees, you will need to distribute this key.

8. Back at the Network Connections window, right-click on the VPN connection and click Connect / Disconnect.
9. Find your VPN profile and click Connect.
10. Enter your user name and password. Click OK.
Was this article helpful?
Related Articles
The VPN:
The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP.
The Encryption Method:
Along with the L2TP/IP protocol the Meraki client VPN employs the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase 2. Best practice dictated that the shared secret should not contain special characters at the beginning or end.
Enabling Client VPN:
Select Enabled from the Client VPN server pull-down menu on the Security Appliance -> Configure -> Client VPN page. You can then configure the following options:
- Client VPN Subnet: The subnet that will be used for Client VPN connections. This should be a private subnet that is not in use anywhere else in your network. The MX will be the default gatway on this subnet and will route traffic to and from this subnet.
- DNS Nameservers: The servers VPN Clients will use to resolve DNS hostnames. You can choose from Google Public DNS, OpenDNS, or specifying custom DNS servers by IP address.
- WINS: If you want your VPN clients to use WINS to resolve NetBIOS names, select Specify WINS Servers from the drop-down and enter the IP addresses of the desired WINS servers.
- Secret: The shared secret that will be used to establish the Client VPN connection.
- Authentication: How VPN Clients will be authenticated.
- Systems Manager Sentry VPN Security: Configuration settings for whether devices enrolled in systems manager should receive a configuration to connect to the Client VPN.
Authentication:
The VPN uses both pre-shared key based authentication and user authentication. To set up the user authentication mechanism, you will need to select your authentication method.
Meraki Cloud Authentication:
Use this option if you do not have an Active Directory or RADIUS server, or if you wish to manager your VPN users via the Meraki cloud. To add or remove users, the User Management section at the bottom of the page. Add a user by selecting “Add new user” and entering the following information:
- Name: Enter the user’s name
- Email: Enter the user’s email address
- Password: Enter a password for the user or select “Generate” to automatically generate a password
- Authorized: Select whether this user is authorized to use the Client VPN
In order to edit an existing user, click on the user under User Management section. To delete a user, click the X next to the user on the right side of the user list. When using Meraki hosted authentication, the user’s email address is the username that is used for authentication.
RADIUS:
Use this option to authenticate users on a RADIUS server. Click Add a RADIUSserver to configure the server(s) to use. You will need to enter the IP address of the RADIUS server, the port to be used for RADIUS communication, and the shared secret for the RADIUS server.
Active Directory:
Use this option if you want to authenticate your users with Active Directory domain credentials. You will need to provide the following information:
- Short Domain: The short name of your Active Directory domain.
- Server IP: The IP address of an Active Directory server on the MX LAN.
- Domain Admin: The domain administrator account the MX should use to query the server.
- Password: Password for the domain administrator account.
For example, considering the following scenario: You wish to authenticate users in the domain test.company.com using an Active Directory server with IP 172.16.1.10. Users normally log into the domain using the format ‘test/username’ and you have created a domain administrator account with the username ‘vpnadmin’ and the password ‘vpnpassword’.
- The Short domain would be ‘test’.
- The Server IP would be 172.16.1.10
- The Domain admin would be ‘vpnadmin’
- The Password would be ‘vpnpassword’.

At this time, the MX does not support mapping group policies via Active Directory for users connecting through the Client VPN. Off road crossover.
Systems Manager Sentry VPN Security:
When using Meraki cloud authentication, Systems Manager Sentry VPN security can be configured. If your Dashboard organization contains one or more MDM networks. Systems Manager Sentry VPN security allows for your devices enrolled in Systems Manager to receive the configuration to connect to the Client VPN through the Systems Manager profile on the device.
To enable Systems Manager Sentry VPN security, choose Enabled from the Client VPN server pulldown menu on the Security Appliance -> Configure -> Client VPN page. You can configure the following options:
- Install Scope: The install scope allows you to select a set of Systems Manager tags for a particular MDM network. Devices with these tags applied in a Systems Manager network will receive a configuration to connect to this network’s Client VPN server through their Systems Manager profile.
- Send All Traffic: Select whether all client traffic should be sent to the MX.
- Proxy: Whether a proxy should be used for this VPN connection. This can be set to automatic, manual, or disabled.
When using Systems Manager Sentry VPN security, the username and password used to connect to the client VPN are generated by the Meraki cloud. Usernames are generated based on a hash of unique identifier on the device and the username of that device. Passwords are randomly generated.
Meraki Vpn Split Tunnel
Was this article helpful?
Meraki Setup Vpn Windows 10
Related Articles
